SHARED INTEL Q&A: Everything the Cisco-Splunk merger tells us about the rise of SIEMs
The Last Watchdog
OCTOBER 17, 2023
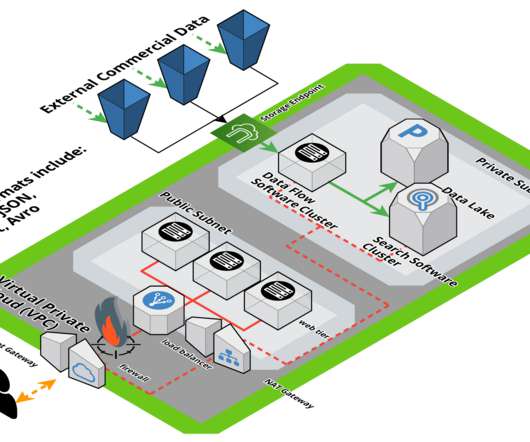
LW: Why are suppliers of legacy firewall, vulnerability management and EDR solutions also now integrating SIEM capabilities? We use machine learning models on open choice big data lakes to detect unknown threats early in the attack chain. Security teams needed greater visibility across their operating environment.




















Let's personalize your content