The Weakest Link: Managing Supply Chain Risk
Approachable Cyber Threats
DECEMBER 21, 2023
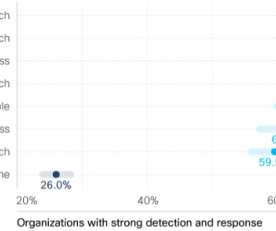
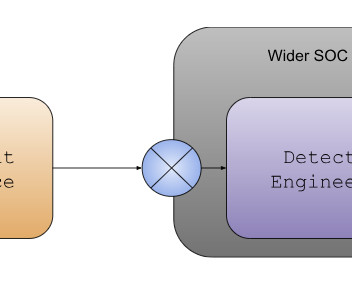
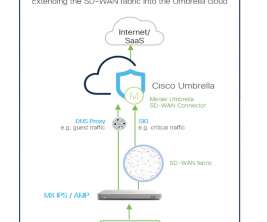
Category Cybersecurity Fundamentals, Third Party Risk Risk Level In the interconnected web of modern business ecosystems, supply chain risks have emerged as insidious threats, leaving even the most vigilant organizations vulnerable to devastating cyber breaches. Why does it seem like supply chain attacks are increasing?
















































Let's personalize your content