Updated Kmsdx botnet targets IoT devices
Security Affairs
AUGUST 28, 2023
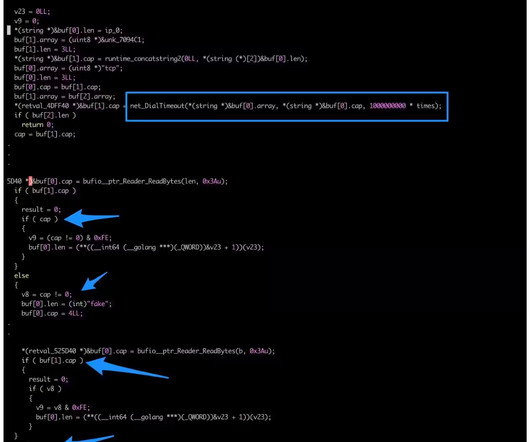
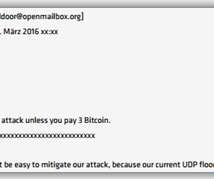
Researchers spotted an updated version of the KmsdBot botnet that is now targeting Internet of Things (IoT) devices. The Akamai Security Intelligence Response Team (SIRT) discovered a new version of the KmsdBot botnet that employed an updated Kmsdx binary targeting Internet of Things (IoT) devices.


















Let's personalize your content