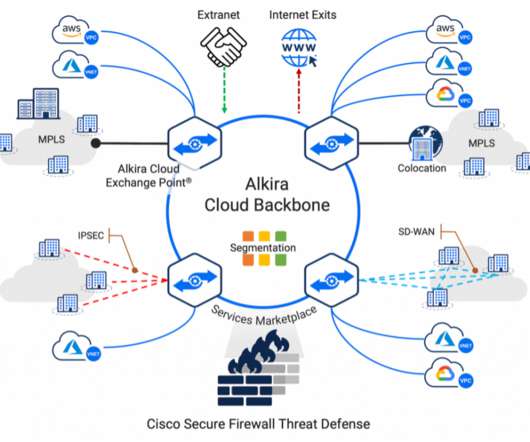
Building a secure and scalable multi-cloud environment with Cisco Secure Firewall Threat Defense on Alkira Cloud
Cisco Security
FEBRUARY 2, 2023
These applications/workloads move to, and reside in multi-cloud architecture, adding complexity to connectivity, visibility, and control. Cisco Secure Firewall Threat Defense Virtual provides unmatched security controls such as stateful firewalling, Snort3 IPS, URL filtering, malware defense, application visibility and control, and more.

















































Let's personalize your content