Practical coexistence attacks on billions of WiFi chips allow data theft and traffic manipulation
Security Affairs
DECEMBER 13, 2021
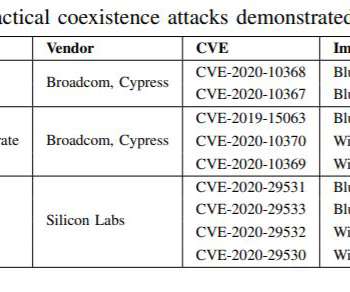
Boffins discovered bugs in WiFi chips that can be exploited to extract passwords and manipulate traffic by targeting a device’s Bluetooth component. Threat actors can execute code by exploiting an unpatched or new security issue over-the-air, or abusing the local OS firmware update mechanism. ” concludes the paper.

























Let's personalize your content