Second-ever UEFI rootkit used in North Korea-themed attacks
Security Affairs
OCTOBER 5, 2020
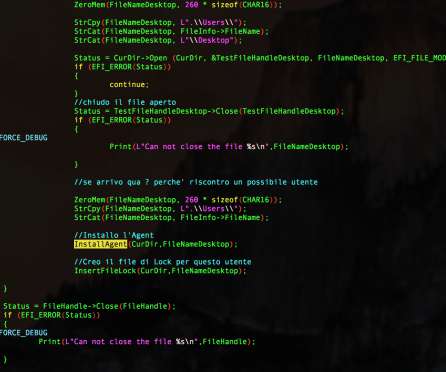
A China-linked threat actor used UEFI malware based on code from Hacking Team in attacks aimed at organizations with an interest in North Korea. Researchers from Kaspersky have spotted a UEFI malware that was involved in attacks on organizations with an interest in North Korea. ” concludes the report.












Let's personalize your content