Measuring the Security of IoT Devices
Schneier on Security
OCTOBER 3, 2019
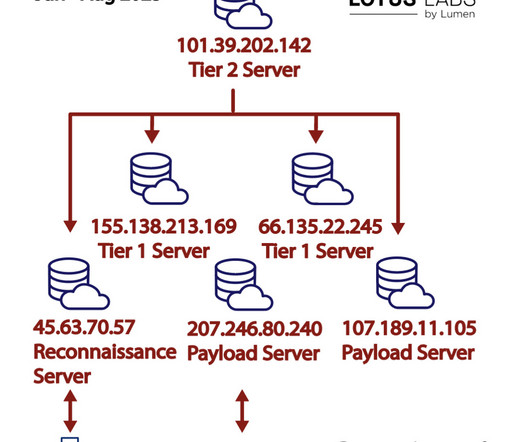
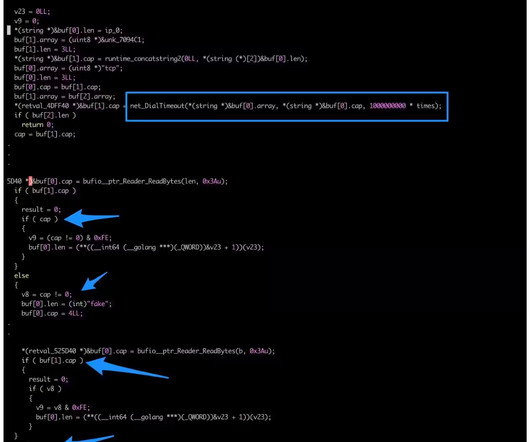
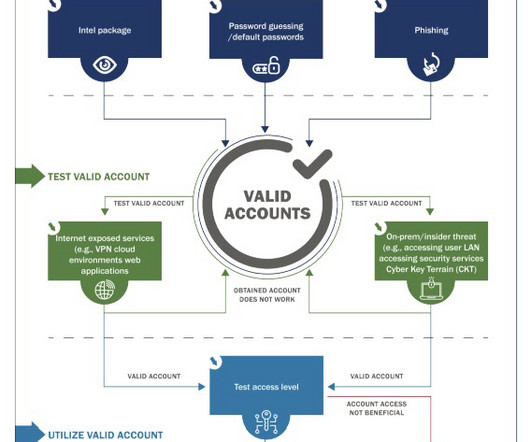
In August, CyberITL completed a large-scale survey of software security practices in the IoT environment, by looking at the compiled software. It represents a wide range of either found in the home, enterprise or government deployments. MIPS is both the most common CPU architecture and least hardened on average.















































Let's personalize your content