Flaws in mobile Internet protocol GTP allow hackers to target 5G users
Security Affairs
JUNE 15, 2020
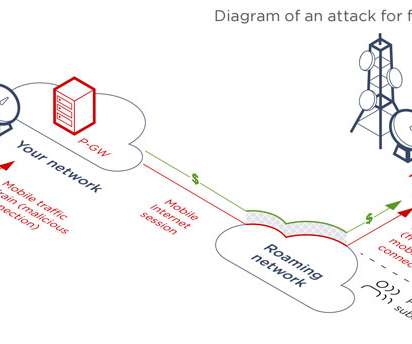
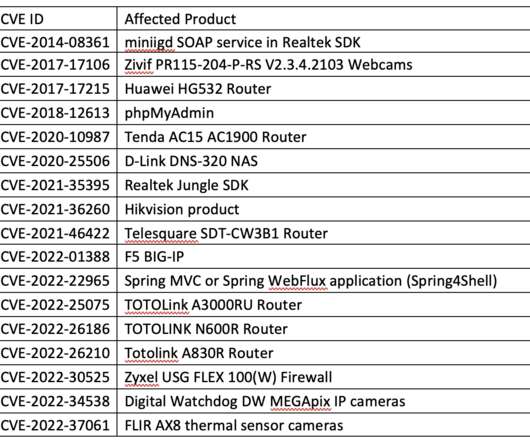
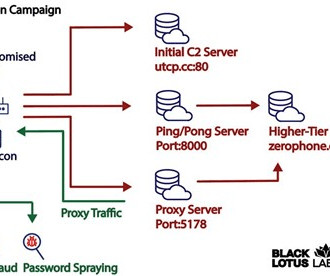
The second architectural flaw is related subscriber credentials that are checked on S-GW (SGSN) equipment by default. phone number) of a real subscriber and impersonate him to access the Internet. “On all tested networks, it was possible to use mobile Internet at the expense of both other subscribers and the operator.”



























Let's personalize your content