ENISA publishes a Threat Landscape for 5G Networks
Security Affairs
NOVEMBER 21, 2019
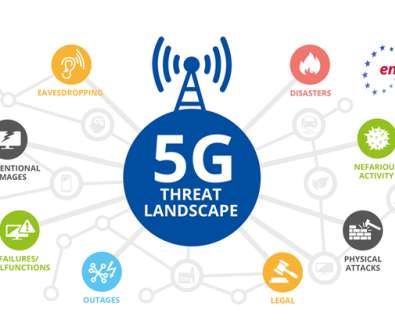
ENISA, the European Union Agency for Cybersecurity publishes a Threat Landscape for 5G Networks, assessing the threats related to the fifth generation of mobile telecommunications networks (5G). 5G infrastructures possess a high degree of complexity due to the multiple features introduced by this technology.



















Let's personalize your content