NetWORK: Redefining Network Security
Cisco Security
MAY 17, 2021
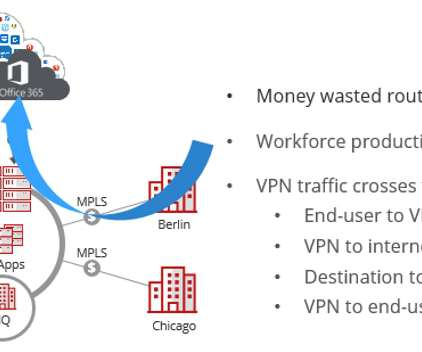
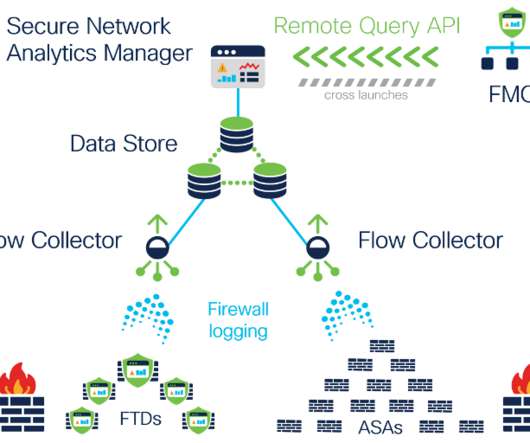
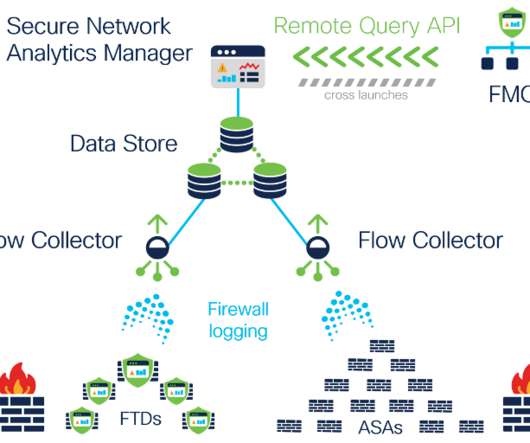
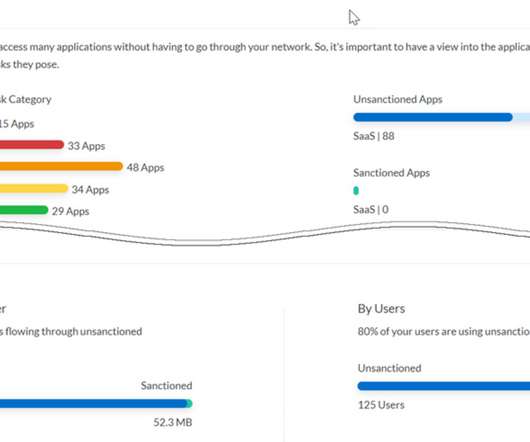
Among the most consequential is Secure Firewall Threat Defense 7.0, We’ve increased throughput by up to 30%—across enabled AVC, IPS, and VPN services—for the majority of Cisco Secure Firewalls. Today, we’re also announcing a new way forward: NetWORK security. Security is too complicated. The new Snort 3 IPS.













































Let's personalize your content