Quantum Computing's Impact on Cybersecurity and the Road Ahead
SecureWorld News
FEBRUARY 24, 2025
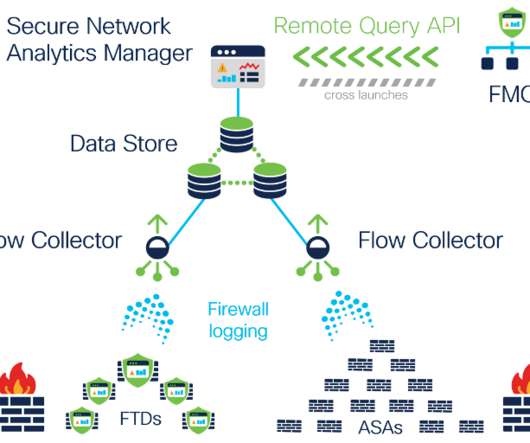
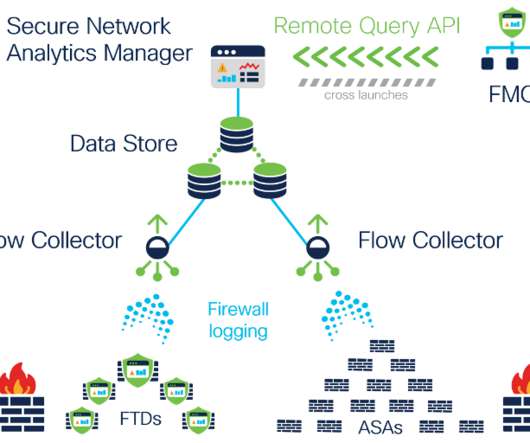
Quantum-powered cybersecurity solutions also present significant opportunities, specifically when looking at threat detection and intrusion response. Another crucial application is quantum-enhanced AI for threat detection and anomaly analysis.

















































Let's personalize your content