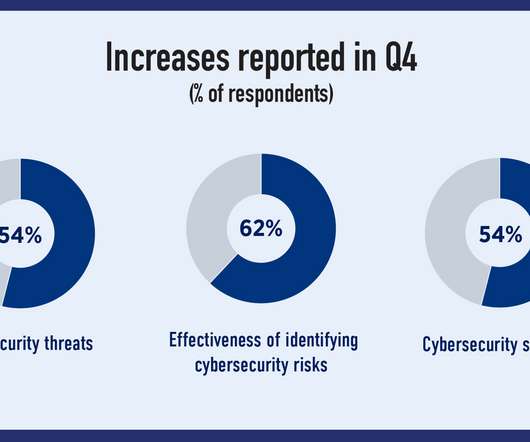
China Says U.S. Hacking Huawei Since 2009
SecureWorld News
SEPTEMBER 28, 2023
In a tale as old as the computer, China has once again pointed fingers at the United States, accusing it of hacking into one of its technology companies. are currently engaged in a fierce battle for technological supremacy, particularly in the rapidly advancing field of artificial intelligence.





























Let's personalize your content