5 API Vulnerabilities That Get Exploited by Criminals
Security Affairs
NOVEMBER 22, 2022
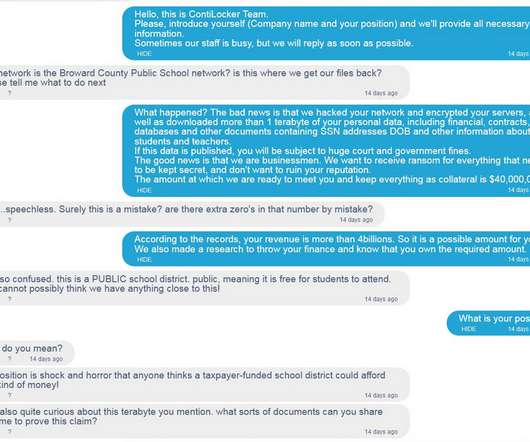
In its API Security Top 10 , the Open Web Application Security Project (OWASP) identifies the top ten threats to APIs. Broken Object Level Authentication (BOLA). APIs with broken object level authentication allow attackers to easily exploit API endpoints by manipulating the ID of an object sent within an API request.


















Let's personalize your content