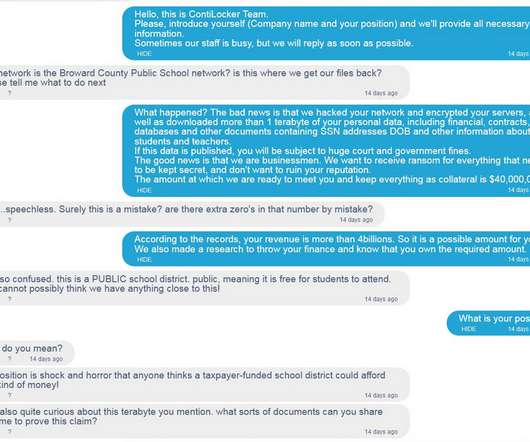
Why Google Passkey is Good for B2B Adoption of Emerging Authentication Practices
Security Boulevard
JUNE 7, 2023
Passkey technology – a new type of passwordless authenticator – is still in the early. The post Why Google Passkey is Good for B2B Adoption of Emerging Authentication Practices appeared first on Axiad.









































Let's personalize your content