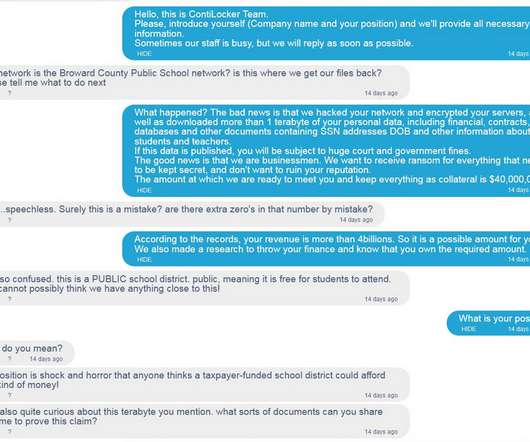
Talos discovered Spelevo EK, an exploit kit spreading via B2B Website
Security Affairs
JUNE 28, 2019
The post Talos discovered Spelevo EK, an exploit kit spreading via B2B Website appeared first on Security Affairs. . ~ Copyright (C) 2014 Media.net Advertising FZ-LLC All Rights Reserved -->. Pierluigi Paganini. SecurityAffairs – Spelevo EK, hacking).

































Let's personalize your content