Canadian government impacted by data breaches of two of its contractors
Security Affairs
NOVEMBER 20, 2023
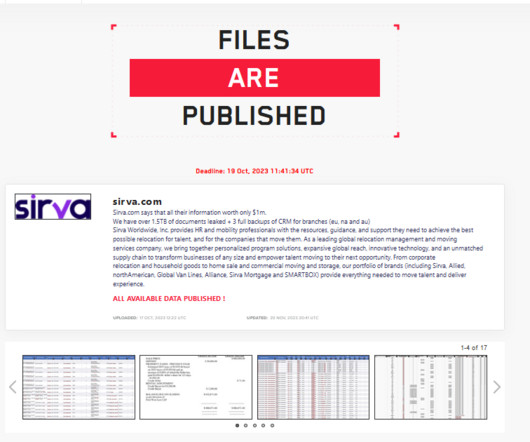
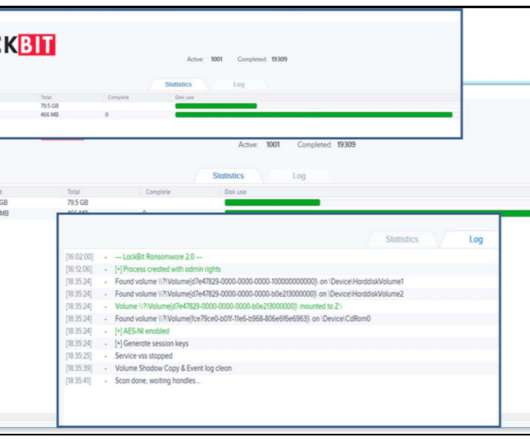
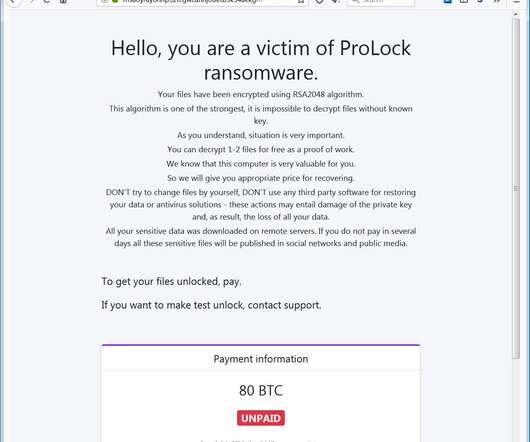
The Canadian government discloses a data breach after threat actors hacked two of its contractors. Data belonging to current and former Government of Canada employees, members of the Canadian Armed Forces and Royal Canadian Mounted Police personnel have been also exposed. Both contractors suffered a security breach in October.















































Let's personalize your content