10,000 organisations targeted by phishing attack that bypasses multi-factor authentication
The State of Security
JULY 14, 2022
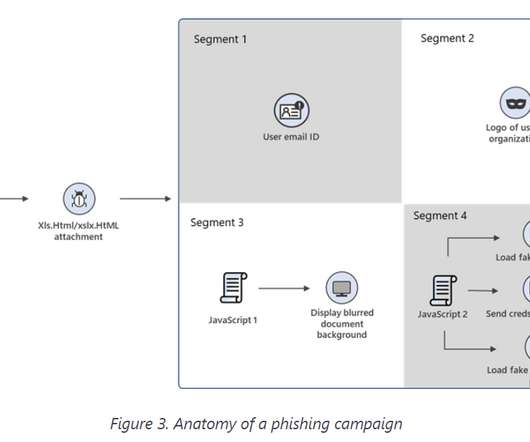
Microsoft has shared details of a widespread phishing campaign that not only attempted to steal the passwords of targeted organisations, but was also capable of circumventing multi-factor authentication (MFA) defences. Read more in my article on the Tripwire State of Security blog.












































Let's personalize your content