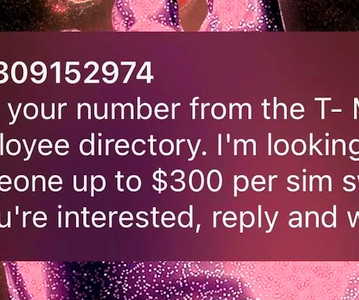
SIM Swappers Try Bribing T-Mobile and Verizon Staff $300
Security Boulevard
APRIL 16, 2024
Not OK: SMS 2FA — Widespread spam targets carrier employees, as scrotes try harder to evade two-factor authentication. The post SIM Swappers Try Bribing T-Mobile and Verizon Staff $300 appeared first on Security Boulevard.






















Let's personalize your content