How to Protect My Business from Identity Theft?
Identity IQ
FEBRUARY 17, 2022
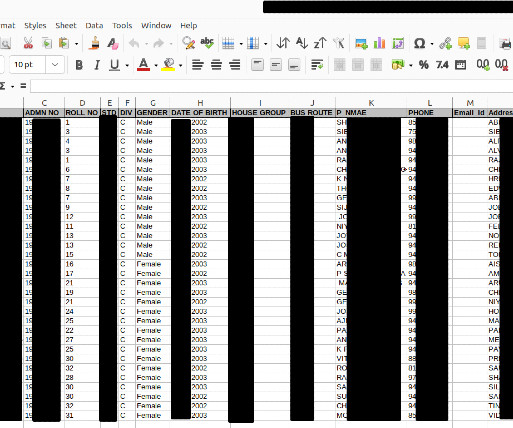
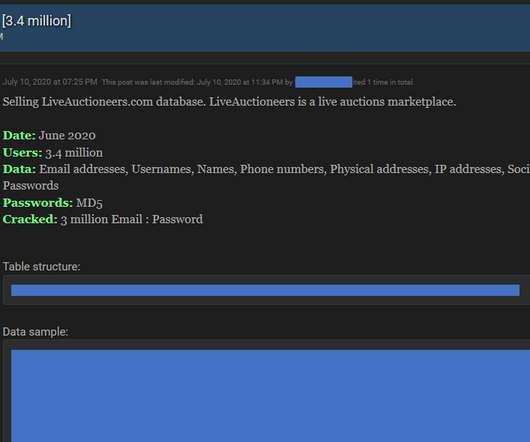
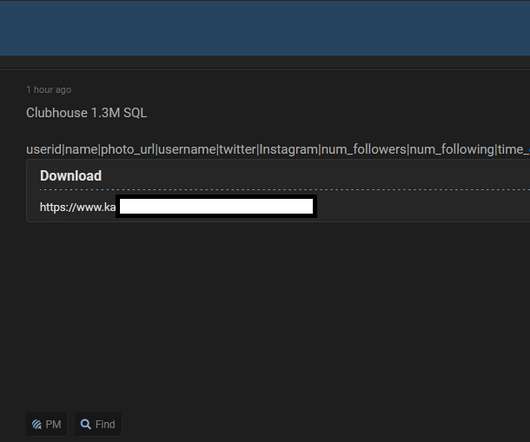
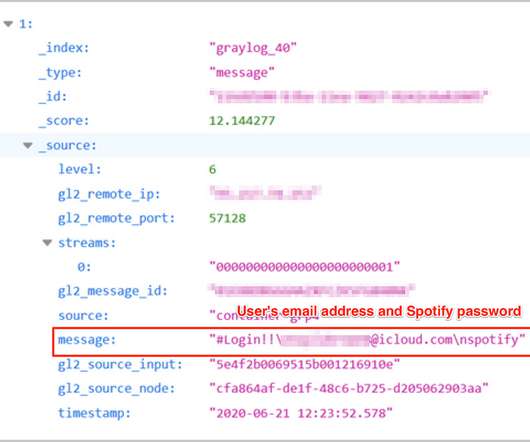
How to Protect My Business from Identity Theft? According to recent reports, identity theft is on the rise. Javelin Strategy reported identity theft resulted in an annual loss of $56 million in a mixed result of different criminal and fraudulent activities last year. Common Types of Business Identity Thefts.











































Let's personalize your content