Passkeys vs. Passwords: The State of Passkeys on Cloud Platforms
Duo's Security Blog
SEPTEMBER 6, 2023
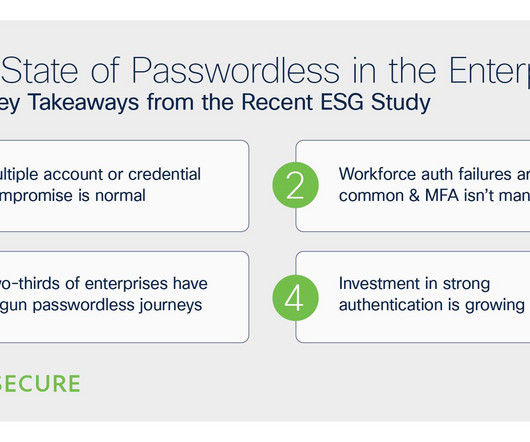
But conventional protection solutions, like password security, fall short when it comes to efficacy. We have a lot of thoughts on passkeys – some of which we’ve shared in other posts in this passkey blog series – and today we’re going to explore how passkeys stack up against passwords from the perspective of cloud platforms.








































Let's personalize your content