Verified Duo Push Makes MFA More Secure
Duo's Security Blog
AUGUST 25, 2022
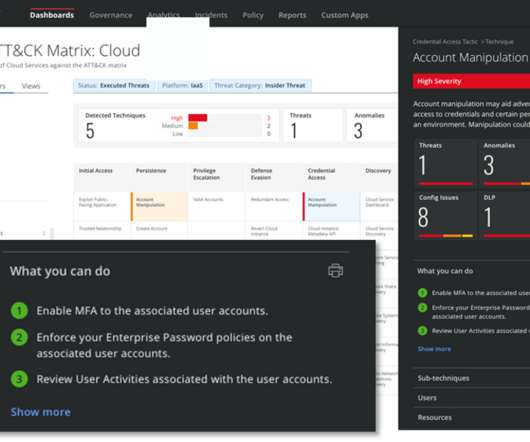
We’re excited to announce early access release of the Verified Duo Push, which will increase the security of our push-based multi-factor authentication (MFA) solution. With modern phishing-resistant authentication methods, we need to ensure that organizations continue to have the best security around push-based MFA.































Let's personalize your content