Protect Your Organization from Cybercrime-as-a-Service Attacks
Thales Cloud Protection & Licensing
OCTOBER 11, 2023
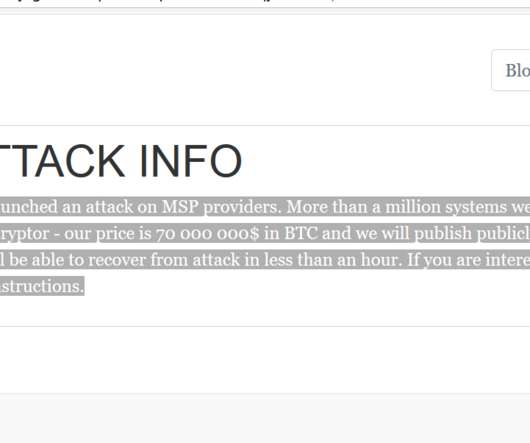
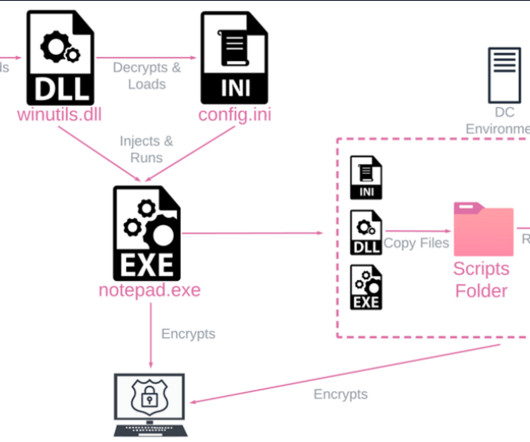
Protect Your Organization from Cybercrime-as-a-Service Attacks madhav Thu, 10/12/2023 - 04:53 In years gone by, only large enterprises needed to be concerned with cybercrime. However, Cybercrime-as-a-Service (CaaS) offerings have essentially democratized cybercrime. What is Cybercrime-as-a-Service?















































Let's personalize your content