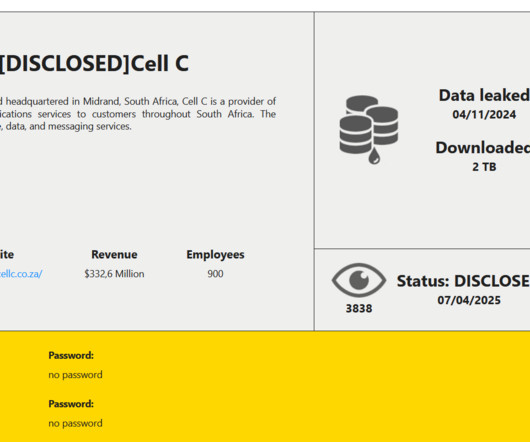
South African telecom provider Cell C disclosed a data breach following a cyberattack
Security Affairs
APRIL 13, 2025
Cell C, one of the biggest telecom providers in South Africa confirms a data breach following a 2024 cyberattack. The company founded in 2001 offers prepaid and postpaid mobile plans, data bundles and internet services, fiber broadband, roaming and international calling, SIM-only plans and device deals.















































Let's personalize your content