Data collection cheat sheet: how Parler, Twitter, Facebook, MeWe’s data policies compare
Security Affairs
JANUARY 13, 2021
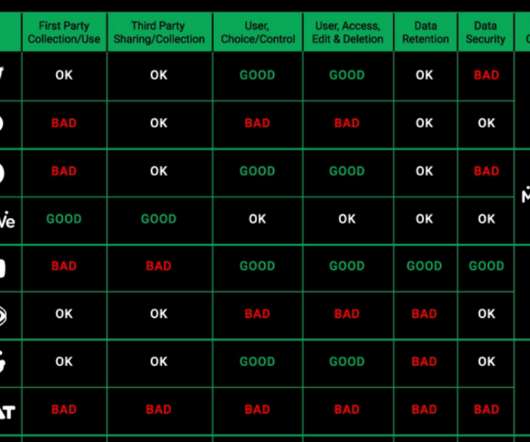
While these alt platforms largely position themselves as “free speech” alternatives, we at CyberNews were also interested in how these alt social platforms compare in terms of data collection. Users would need to read both Triller’s and Quickblox’ privacy policies to get a good idea of how their data is being collected and processed.

























Let's personalize your content