ESET found a variant of the Hive ransomware that encrypts Linux and FreeBSD
Security Affairs
OCTOBER 29, 2021
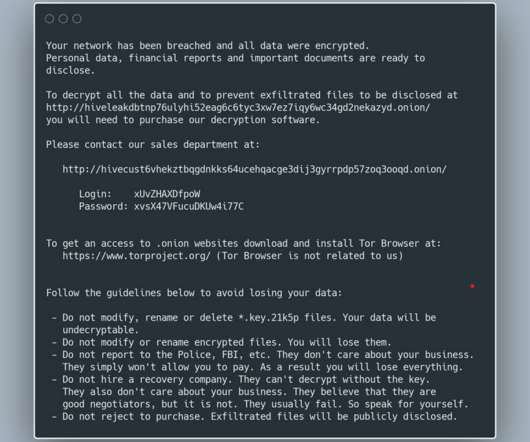
The Hive ransomware operators have developed a new variant of their malware that can encrypt Linux and FreeBSD. ESET researchers discovered a new Hive ransomware variant that was specifically developed to encrypt Linux and FreeBSD. The Hive ransomware adds the.hive extension to the filename of encrypted files. .



















Let's personalize your content