LastPass Devs Were Phished for Credentials
Security Boulevard
MARCH 1, 2023
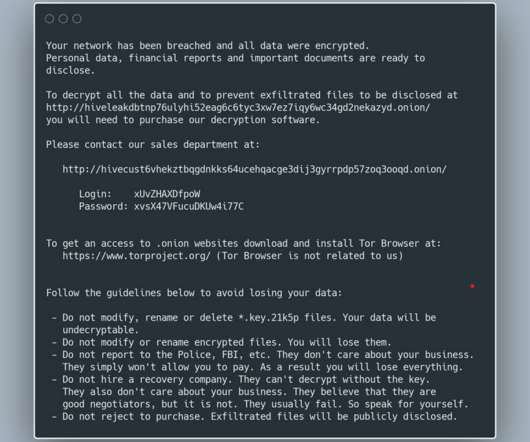
LastPass has followed news of last month’s breach with details on a second attack in which developers were phished for their credentials. In the January incident, the password manager’s parent, GoTo, said that in addition to stealing encrypted backups containing customer data, hackers nicked an encryption key last November. “An
















































Let's personalize your content