MyBook Users Urged to Unplug Devices from Internet
Krebs on Security
JUNE 25, 2021
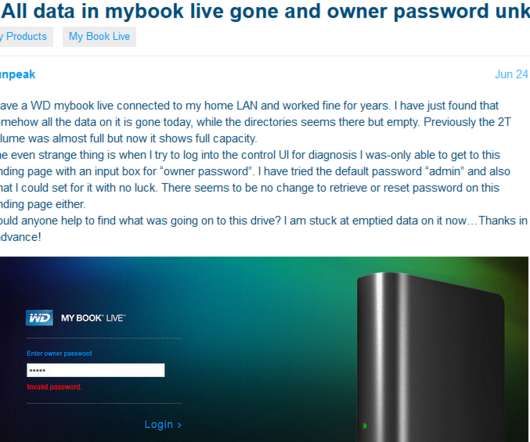
Hard drive giant Western Digital is urging users of its MyBook Live brand of network storage drives to disconnect them from the Internet, warning that malicious hackers are remotely wiping the drives using a critical flaw that can be triggered by anyone who knows the Internet address of an affected device.






















Let's personalize your content