Akira ransomware targets Finnish organizations
Security Affairs
JANUARY 13, 2024
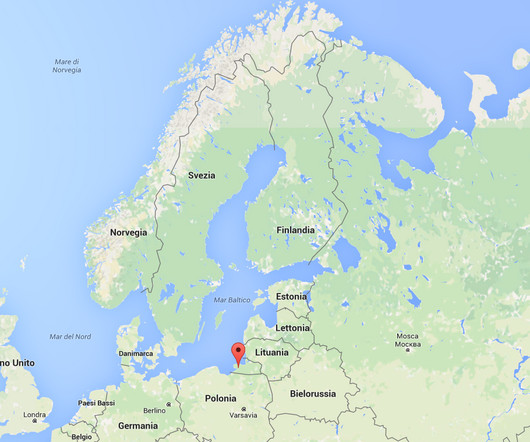
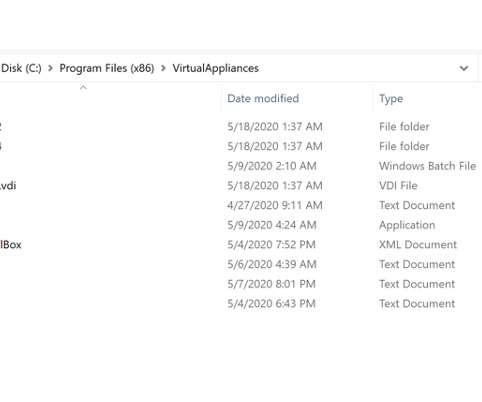
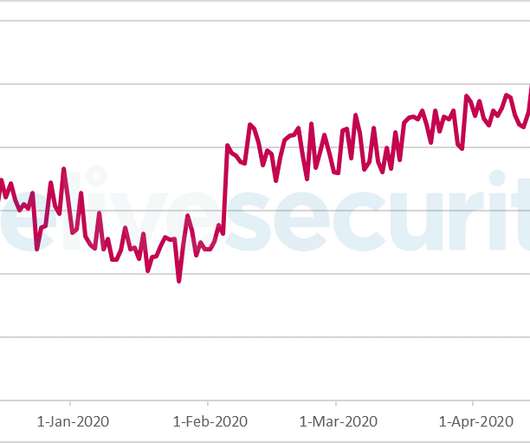
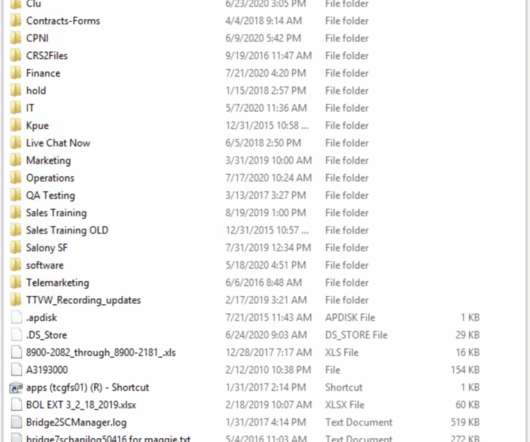
The Finish National Cybersecurity Center (NCSC-FI) warns of increased Akira ransomware attacks targeting NAS and tape backup devices of organizations in the country. Threat actors are wiping NAS and backup devices. Cisco investigated the hacking campaign with the help of Rapid7.














































Let's personalize your content