Florence, Ala. Hit By Ransomware 12 Days After Being Alerted by KrebsOnSecurity
Krebs on Security
JUNE 9, 2020
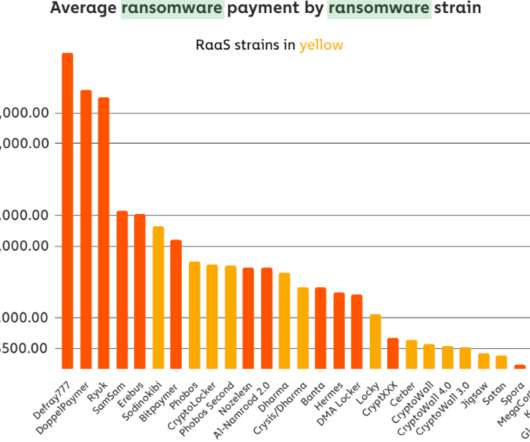
that their information technology systems had been infiltrated by hackers who specialize in deploying ransomware. In late May, KrebsOnSecurity alerted numerous officials in Florence, Ala. Nevertheless, on Friday, June 5, the intruders sprang their attack, deploying ransomware and demanding nearly $300,000 worth of bitcoin.
























Let's personalize your content