News alert: Criminal IP and Quad9 collaborate to exchange domain and IP threat intelligence
The Last Watchdog
MAY 13, 2024
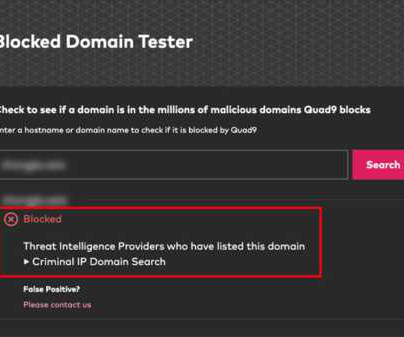
Through this integration, Quad9 leverages the most up-to-date threat intelligence lists, incorporating data from Criminal IP’s database of malicious domains to block harmful hostnames. Quad9 is operated as a non-profit by the Quad9 Foundation in Switzerland for the purpose of improving the privacy and cybersecurity of Internet users.




































Let's personalize your content