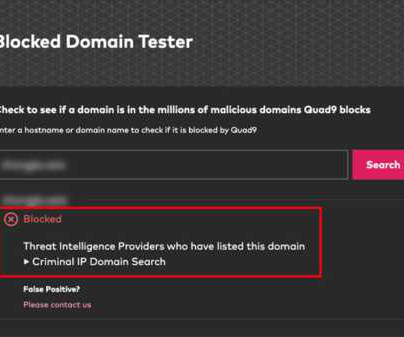
News alert: Criminal IP and Quad9 collaborate to exchange domain and IP threat intelligence
The Last Watchdog
MAY 13, 2024
Through this integration, Quad9 leverages the most up-to-date threat intelligence lists, incorporating data from Criminal IP’s database of malicious domains to block harmful hostnames. The specially designed Criminal IP Malicious Domains Retrieval API is used to send the Domain Data Feed identified as malicious to Quad9 for integration.
















































Let's personalize your content