Identity Threat Trends for Higher Education
Duo's Security Blog
JANUARY 29, 2024
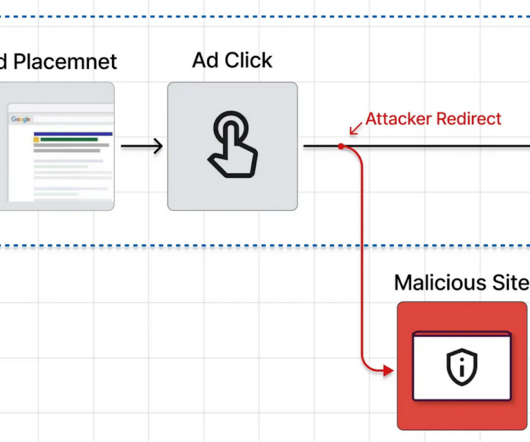
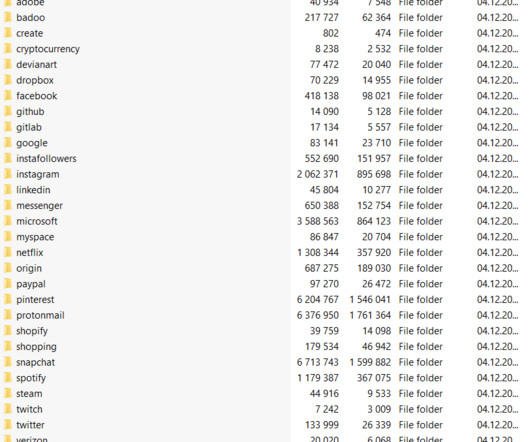
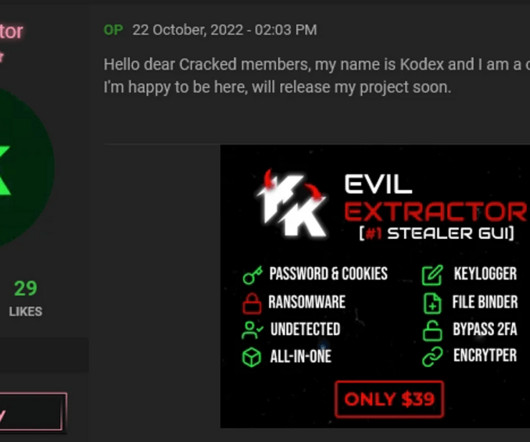
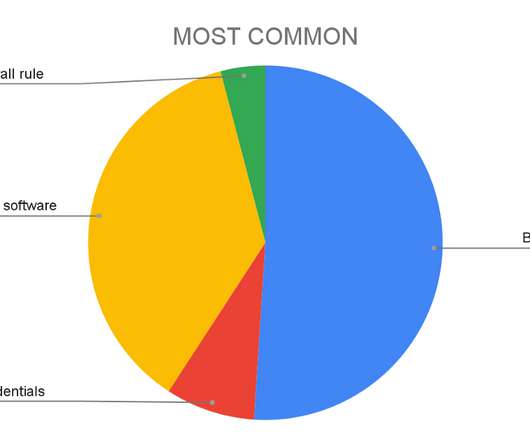
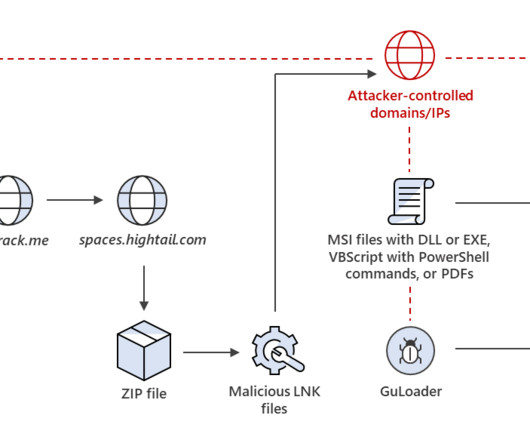
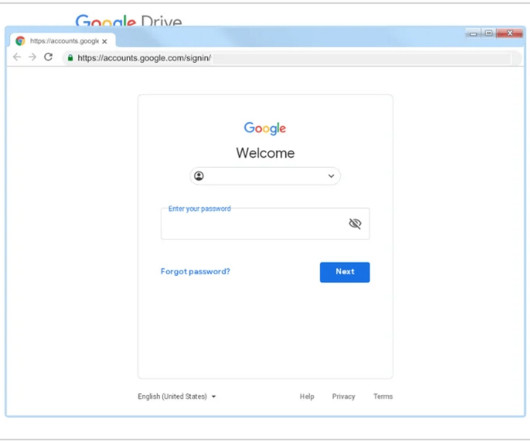
As a new semester begins, we at Cisco Duo want to share some findings and trends pertaining to threat activity we have seen across higher education customers. In this situation, we can assume that they have either phished users’ first factor credentials (their password), or are crawling user accounts with weak, guessable passwords.












































Let's personalize your content