A broken marriage. Abusing mixed vendor Kerberos stacks
Pen Test Partners
AUGUST 24, 2023
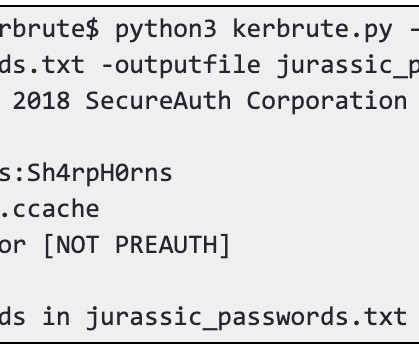
With that in mind, and for those that weren’t able to attend, here’s a follow-up blog post. Accounts are susceptible to user spoofing when providing Kerberos tickets to *nix based services joined to an Active Directory realm. This is usually facilitated through the MIT or Heimdal Kerberos stacks.










Let's personalize your content