Social Engineering 101: What It Is & How to Safeguard Your Organization
Duo's Security Blog
DECEMBER 14, 2023
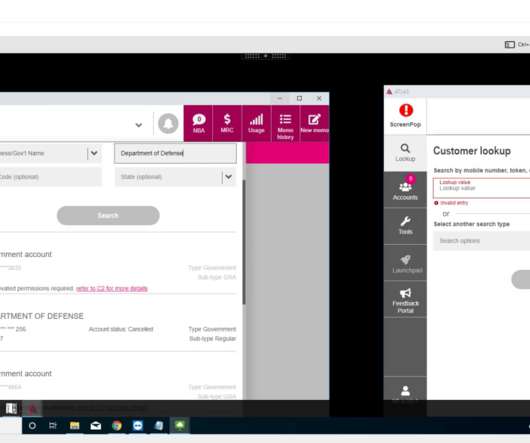
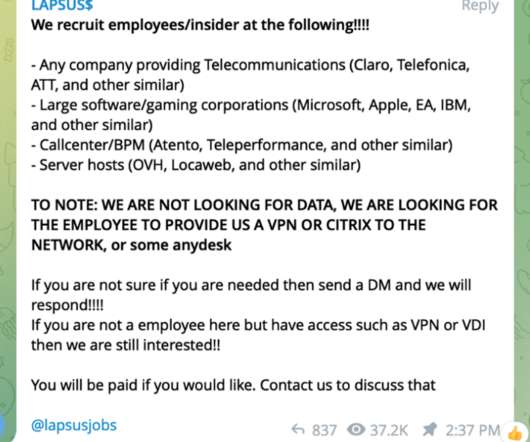
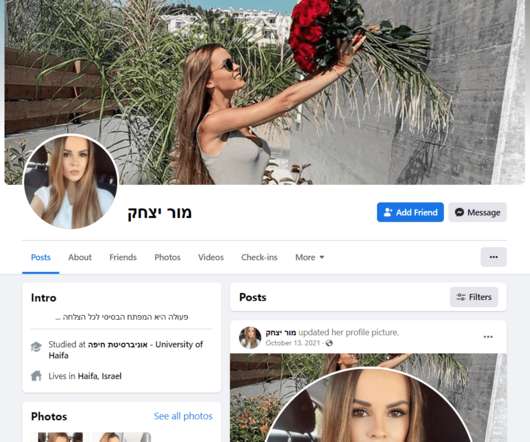
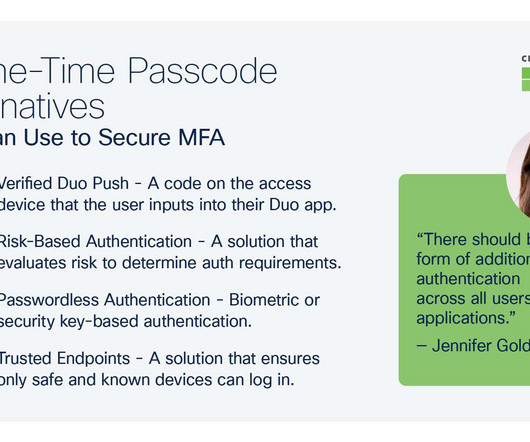
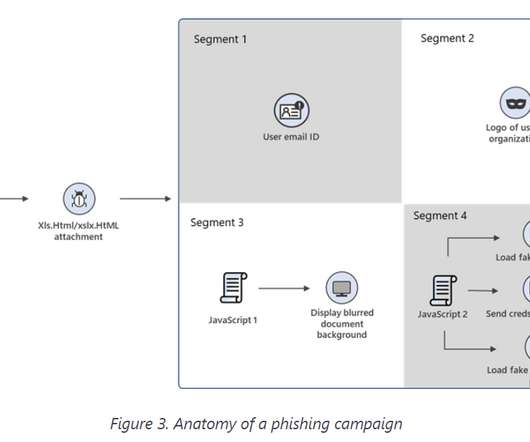
But as it turns out, John was a victim of a phishing scam, a type of social engineering attack where the cybercriminal impersonated John’s IT department to gain his trust and trick him into revealing his login credentials. What is social engineering? This is available in Duo’s Advantage and Premier tiers.













































Let's personalize your content