SYN Flood Explained. How to Prevent this Attack from Taking over your Server
Heimadal Security
FEBRUARY 8, 2023
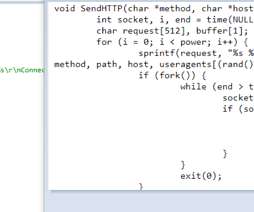
SYN flood is a type of denial-of-service (DoS) attack in which a threat actor floods a server with several requests, but doesn’t acknowledge back the connection, leaving it half-opened, usually with the purpose of consuming server resources, which leads to denying other users access to that server.













Let's personalize your content