“My Slice”, an Italian adaptive phishing campaign
Security Affairs
JANUARY 22, 2024
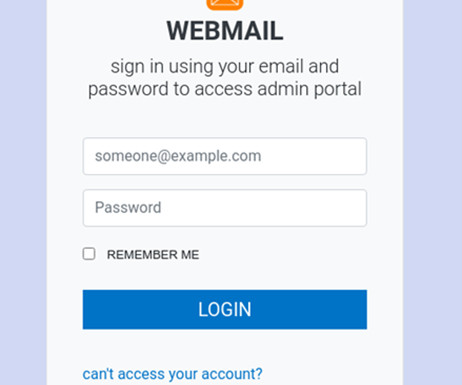
Adaptive phishing campaigns are emerging as an increasingly sophisticated threat in the cybersecurity landscape. The phenomenon This phenomenon represents an evolution of traditional phishing tactics, as attackers seek to overcome defenses using more personalized and targeted approaches.





















Let's personalize your content