Phish or Be Phished. That is the question!
Security Boulevard
SEPTEMBER 7, 2022
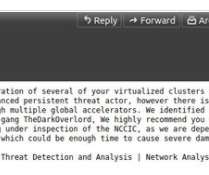
Phish or Be Phished. Email phishing attacks are becoming more challenging to spot. Why did the email provider’s email anti-spam and anti-phish protection layer not quarantine the message? Even with a generic greeting, you would think an AL-powered anti-phishing protection engine would have blocked the message.








































Let's personalize your content