DSPM & AI Are Booming: $17.87B and $4.8T Markets by 2033
Security Affairs
JULY 24, 2025
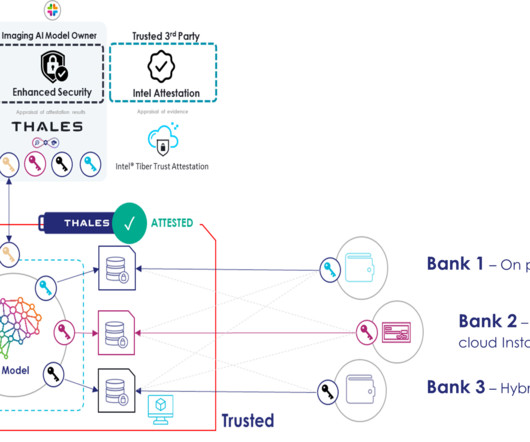
DSPM provides a comprehensive view of an organization’s data security posture, its compliance status, security and privacy threats, and, critically, how to manage these risks effectively. It does so by helping organizations: Discover and classify sensitive data across cloud environments. Continuously monitor data risks.


































Let's personalize your content