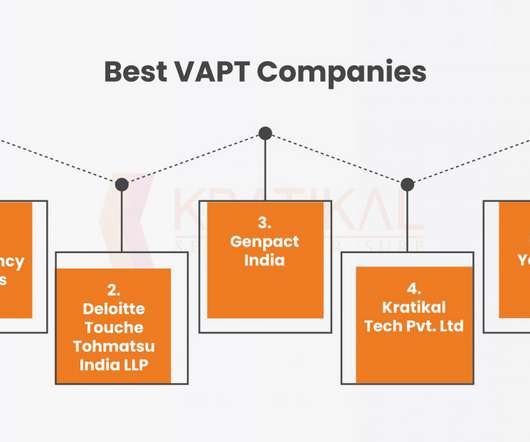
Top VAPT Testing Companies
Security Boulevard
JANUARY 6, 2023
Introduction By reducing information risks and vulnerabilities, a process called information security, also referred to as infosec, protects electronic data. Data can be stored in text, picture, or video file formats on servers, desktop computers, laptops, or mobile devices. InfoSec […].






























Let's personalize your content