LW ROUNDTABLE: Predictive analytics, full-stack visualization to solidify cyber defenses in 2025
The Last Watchdog
DECEMBER 18, 2024
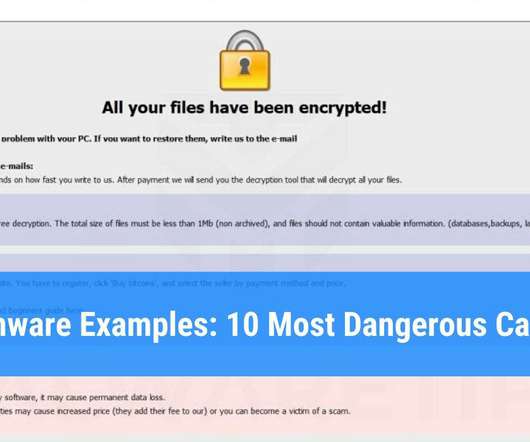
Karl Holmqvist , CEO, Lastwall In 2025, the Steal-Now, Decrypt-Later threat will accelerate post-quantum cryptography (PQC) adoption. Quantum computing advances are making traditional encryption obsolete, and adversaries are stockpiling data for future decryption.



















































Let's personalize your content