New Lobshot hVNC malware spreads via Google ads
Security Affairs
MAY 1, 2023
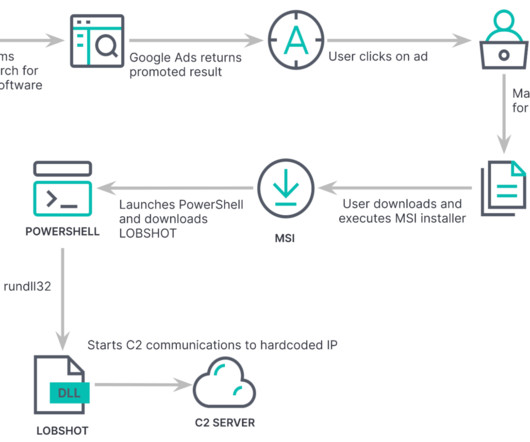
The previously undetected LOBSHOT malware is distributed using Google ads and gives operators VNC access to Windows devices. Threat actors are using an elaborate scheme of fake websites through Google Ads to spread their malware, the backdoors are embedded in installers for apparently legitimate applications, such as AnyDesk.




























Let's personalize your content