Crooks hacked Mandiant X account to push cryptocurrency scam
Security Affairs
JANUARY 4, 2024
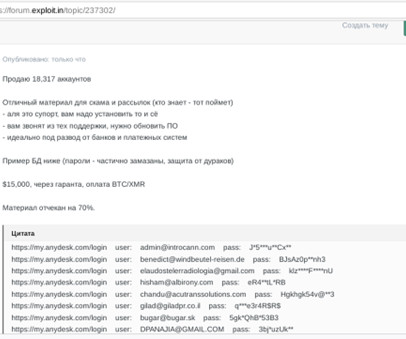
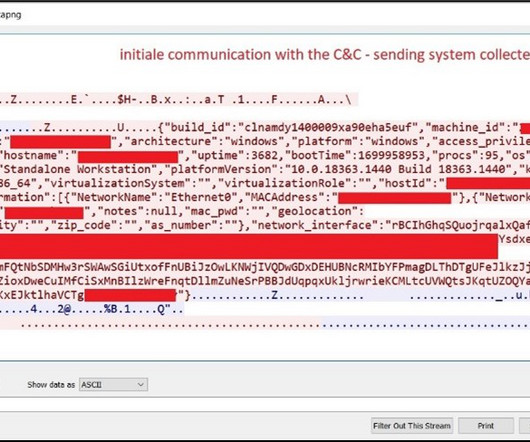
The X account of cybersecurity giant Mandiant was hacked, attackers used it to impersonate the Phantom crypto wallet and push a cryptocurrency scam. Crooks hacked the X account of cybersecurity firm Mandiant and used it to impersonate the Phantom crypto platform and share a cryptocurrency scam.






































Let's personalize your content