Hackers Exploit Zoom's Remote Control Feature in Cryptocurrency Heists
SecureWorld News
APRIL 22, 2025
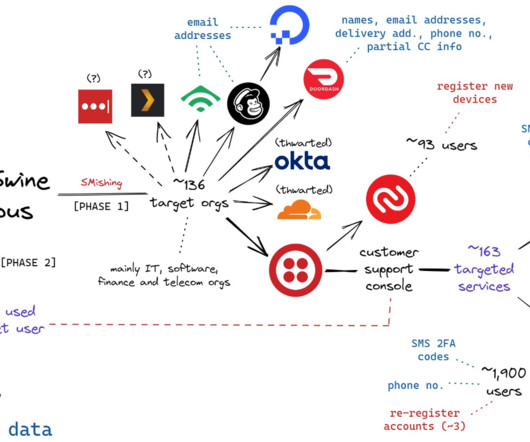
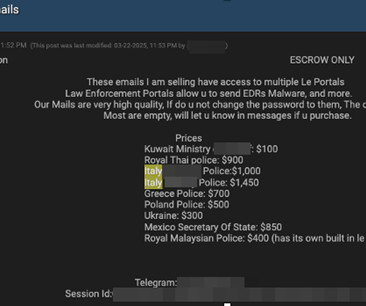
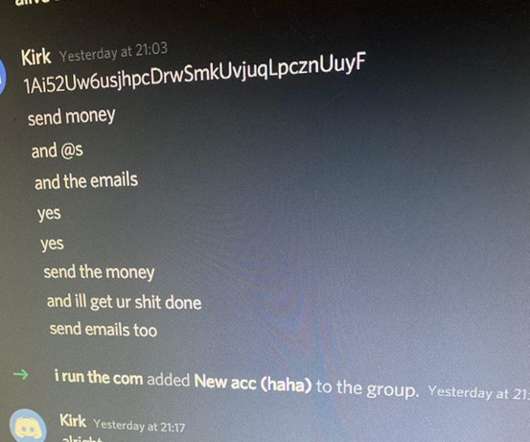
A sophisticated cybercrime campaign, dubbed Elusive Comet , has been uncovered, in which North Korean threat actors are exploiting Zoom's remote control feature to infiltrate the systems of cryptocurrency professionals. The research behind the discovery was released by Security Alliance , which tracked and analyzed the campaign.















































Let's personalize your content