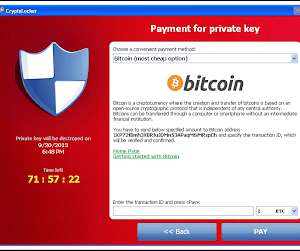
MY TAKE: Cyber attacks on industrial controls, operational technology have only just begun
The Last Watchdog
OCTOBER 8, 2018
Monitoring and management of many existing industrial control systems’ (ICS) embedded devices, like pumps, valves and turbines, are ancient in technological terms. At the operational level, critical industrial sectors are dependent on technology developed 10 to 15 years ago and that aren’t regularly patched.




























Let's personalize your content