Top Cyber Attacker Techniques, August–October 2024
Digital Shadows
NOVEMBER 26, 2024
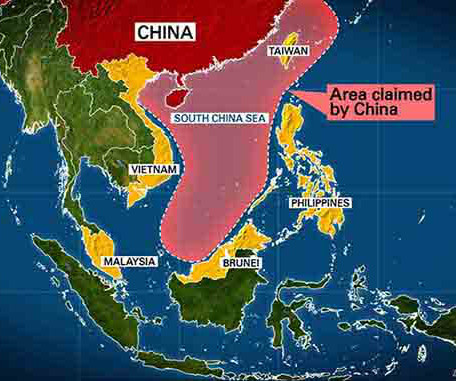
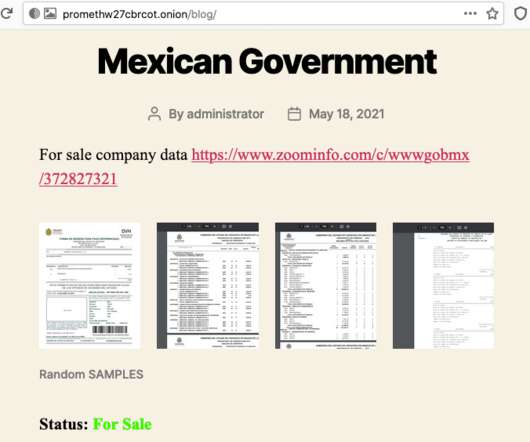
The US, manufacturing sector, and professional, scientific, and technical services (PSTS) sector are primary targets amidst an overall increase in ransomware attacks. Using the MITRE ATT&CK framework, we’ll provide a comprehensive overview of the key cyber threats you need to know about to keep your environment protected.
















































Let's personalize your content