U.S. Sanctions Cloud Provider ‘Funnull’ as Top Source of ‘Pig Butchering’ Scams
Krebs on Security
MAY 29, 2025
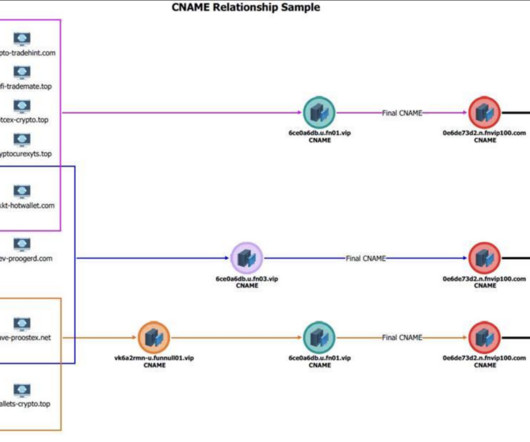
a Philippines-based company that provides computer infrastructure for hundreds of thousands of websites involved in virtual currency investment scams known as pig butchering.” ” The Treasury Department said Funnull’s operations are linked to the majority of virtual currency investment scam websites reported to the FBI.
















































Let's personalize your content